Implementation Details
The LiveWire Omnipeek UI and back-end now use JSON Web Tokens (JWTs), a widely adopted technology in modern web applications. These tokens contain information such as the expiration time (exp), the time the token was issued (iat), a username (name), a not-valid-before time (nbf), a session id (sess), and a user id (sub). JWTs are signed to verify authenticity.
Example
In this screenshot of the Chrome Developer Tools Network Tab, the login API returns a JWT for the authToken in the response along with the tokenType “Bearer”. This is otherwise known as an access token.
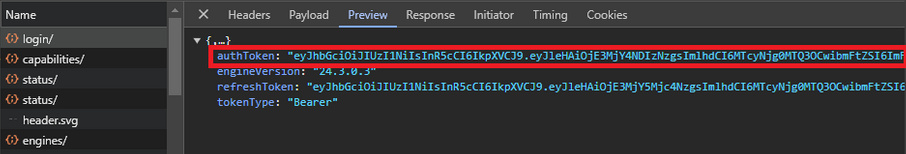
The complete JWT returned is eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3MjY4NDIzNzgsImlhdCI6MTcyNjg0MTQ3OCwibmFtZSI6ImFkbWluIiwibmJmIjoxNzI2ODQxNDc4LCJzZXNzIjoiNjY5M2UzN2FhNDQ2ZDlkNjBkNmUxYTMyNGYzMzk2OTUiLCJzdWIiOiJhZG1pbiJ9.HHTNCdyWKe7inqS8ZA2D5hzWLySRHp4IbXqgbsj5pC4.
The token is in 3 parts: the header, payload, and signature. It is signed using the Authentication Group Secret, mGyHk81TmH4YwIN_qxaFQASKPI9QusfY.
The token can decoded and verified online https://jwt.io/#debugger-io?token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE3MjY4NDIzNzgsImlhdCI6MTcyNjg0MTQ3OCwibmFtZSI6ImFkbWluIiwibmJmIjoxNzI2ODQxNDc4LCJzZXNzIjoiNjY5M2UzN2FhNDQ2ZDlkNjBkNmUxYTMyNGYzMzk2OTUiLCJzdWIiOiJhZG1pbiJ9.HHTNCdyWKe7inqS8ZA2D5hzWLySRHp4IbXqgbsj5pC4.
Compatibility
JWTs are now the default authentication method for the LiveWire Web UI by requesting a tokenType of “Bearer” in the login API. However, the previous authentication method is still supported by engines that do not support JWTs, ensuring backward compatibility.
Security
Since JWTs carry sensitive information, they are always transmitted over encrypted channels (TLS) to prevent eavesdropping. However, if an attacker gains access to a JWT, they could use it to obtain unauthorized access. To mitigate this risk, JWTs used by LiveWire have a short expiration time (15 minutes) and must be periodically renewed using a “refresh token”.
Expiration & Refresh Tokens
When the LiveWire UI requests a JWT from the login API, the engine returns an access token with a short expiration time (15 minutes by default) along with a “refresh token”. The refresh token is used to obtain new access tokens when the current one nears expiration. The web UI will automatically request a new access token about 1 minute before the current token expires.
◦ Remote Engine Connections
The access token is used to connect to remote engines, with the session identified by the session ID in the token. The session will remain active even after a new token is issued.
The access token is used to connect to remote engines, with the session identified by the session ID in the token. The session will remain active even after a new token is issued.
◦ Refresh Token Lifetime
The refresh token also has an expiration time, typically set to 1 day. Both the refresh token and access token lifetimes can be configured in omni.conf by adjusting the refreshtokenlifetime and accesstokenlifetime settings, respectively.
The refresh token also has an expiration time, typically set to 1 day. Both the refresh token and access token lifetimes can be configured in omni.conf by adjusting the refreshtokenlifetime and accesstokenlifetime settings, respectively.